Containing VDI by Falling into a Kasm
Welcome to today's adventure in the world of opensource, an unparalleled tool that is only available to GNU Linux. Now if I was to discuss a great new gui tool, I could rule out over 95% of all global desktop users (not mentioning WSL here). This article would then apply to (quick math) around negative 12% of my readers (rough math after carrying the one and getting a divide by zero error). I am here today to talk about Kasm - the isolation platform for secure remote access.
Why Kasm? Well, tell me if you have ever run across these common business scenarios:
- Need to provide access to internal applications via a common user interface (i.e. like a browser with isolation, or containerized app.)
- Securely leverage a standard toolset of business applications for remote access
- Build a customized environment for training, application isolation, or development
- Oh, and do it on the cheaps
This is the standard use case for most virtual desktop infrastructure adoption. Normally if I were having a customer conversation about Azure my goto would be Azure Virtual Desktop. Azure Virtual Desktop is an enterprise product that enables securely deploying and operational-izing desktop applications securely. It even makes it challenging to discuss competing of even cooper-titoned products like Citrix (because of cost and features).
But and I mean a big but here; what if all I needed were some Linux desktop client apps and with security, operations, and functionality in mind?
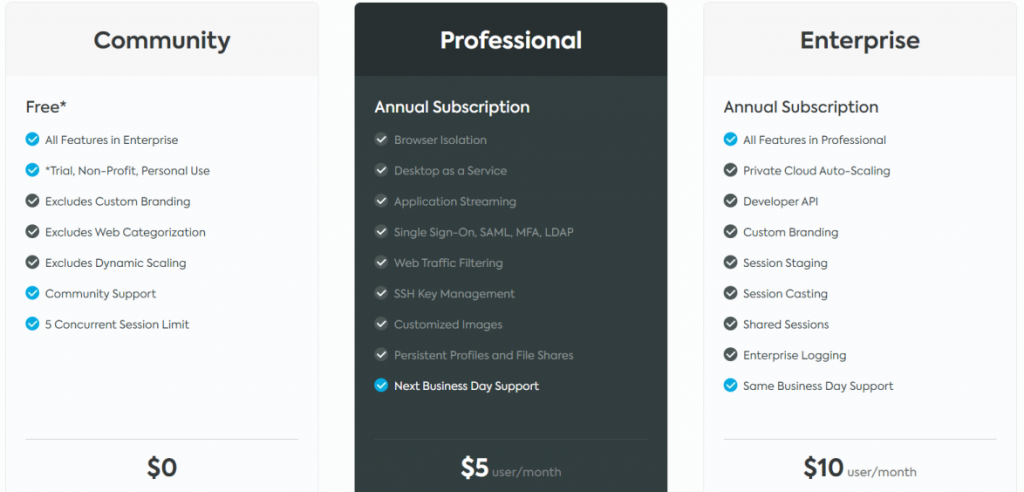
Take a look at Kasm - it has an open source Workspaces Community edition and Workspaces Business editions. There is also a difference between server and cloud based deployments (in the Business editions).
Today I am going to be discussing how to setup a server Community edition in Azure.
There are several ways to solve this:
- Spin up a Linux VM in Azure - please make it at least a little beef-ier than the minimum requirements - System Requirements — Kasm 1.11.0 documentation (kasmweb.com)
- Deploy an Azure Firewall - we need to keep our 'security and controls' people happy by NOT enabling a public IP address on your Linux VM
- Install and Run Kasm - oddly enough the easiest step
- Access your applications - and other stuff
Approach
Spin up a Linux VM in Azure - does require having a subscription and the under the hood infrastructure goodness. Here are a few details to keep in mind while creating this virtual machine. You're going to need a virtual network (with subnetting) to deploy this single vm (or larger subnetting if you are looking deploy the multi-server version). The vnet will require a delegated subnet for the Azure firewall (named appropriately, AzureFirewallSubnet). Do not add a public IP address to the server, as long as you can use Azure Bastion, or vpn to access it. For the vm keep the minimum requirements in mind on both the supported OS (Ubuntu, Debian, etc.) and size (my recommendation here would be a Standard D2s v3 or larger). Lastly, ensure that you meet the storage requirements (because I had to upgrade my virtual hard drive from the default 32 GiB) to Disk tier P6 at 64 GiB, and (if you want to keep this non-ephemeral) add a swap partition (or for Ubuntu).
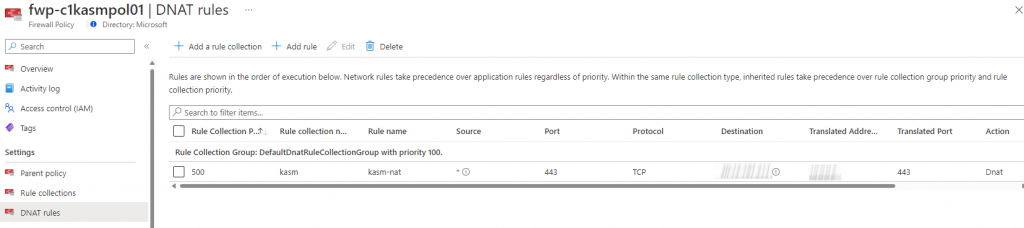
Deploy an Azure Firewall - follow these instructions, specifically the section for setting up a DNAT rule. You will need to know the IP address of your server and the Public IP address of this Azure Firewall so save it for creating the policy. For sake of ease here is a screen from my Firewall Policy. Keep in mind that the Destination is the Public IP address of the Firewall and Translated Address is the IP address of the virtual machine:
Install and Run Kasm - Following the instructions from here, you can walk through this very quickly. I did however make a script, the reason being is that the mount point (/mnt) for the swap is ephemeral. A reboot will kill this installation which candidly is fine by me because I am using this only for testing. (That being said, creating a swap can be done by editing the /etc/waagent.conf file (please create a backup) and edit the following lines:
- ResourceDisk.Format=y
- ResourceDisk.EnableSwap=y
- ResourceDisk.SwapSizeMB={SIZE_OF_SWAP}
In my case for testing I just created a 2048 sized swap. See from this script (if have the swap then just comment out swap creation and mounting section). After running the script or installing it manually you need to remember to enable port 443 on the VM. Easy as 1, 2, 3 from the command line with az command line, or Cloud shell:
- az login
- az account set --subscription "{YOUR_SUBSCRIPTION_NAME}"
- az vm open-port --resource-group "{VM_RESOURCE_GROUP}" --name "{VM_NAME}" --port 443
Save and run the script but be sure to capture and secure the output. As a script, I just export the stdout to a file in my home directory (please secure it with chmod 600 kasm_access.txt) like this:
sudo deploy_kasm.sh > ~/kasm_access.txt; chmod 600 ~/kasm_access.txt
Script for reference:
Script
#!/bin/bash ## This script creates a swap partition and installs Kasm ## This just creates the 2GB swap partition in an ephemeral FS sudo fallocate -l 2g /mnt/2GiB.swap sudo chmod 600 /mnt/2GiB.swap sudo mkswap /mnt/2GiB.swap sudo swapon /mnt/2GiB.swap ## Install Kasm 1.11.0.18142e cd /tmp curl -O https://kasm-static-content.s3.amazonaws.com/kasm_release_1.11.0.18142e.tar.gz">https://kasm-static-content.s3.amazonaws.com/kasm_release_1.11.0.18142e.tar.gz tar -xf kasm_release*.tar.gz sudo bash kasm_release/install.sh
Access your applications - now open your favorite browser and login with the supplied credentials (i.e. supplied in the output of the installation) and you should see a screen like this:

Once in simply click on any application to launch. This runs the containerized application on the server and establishes the client session.
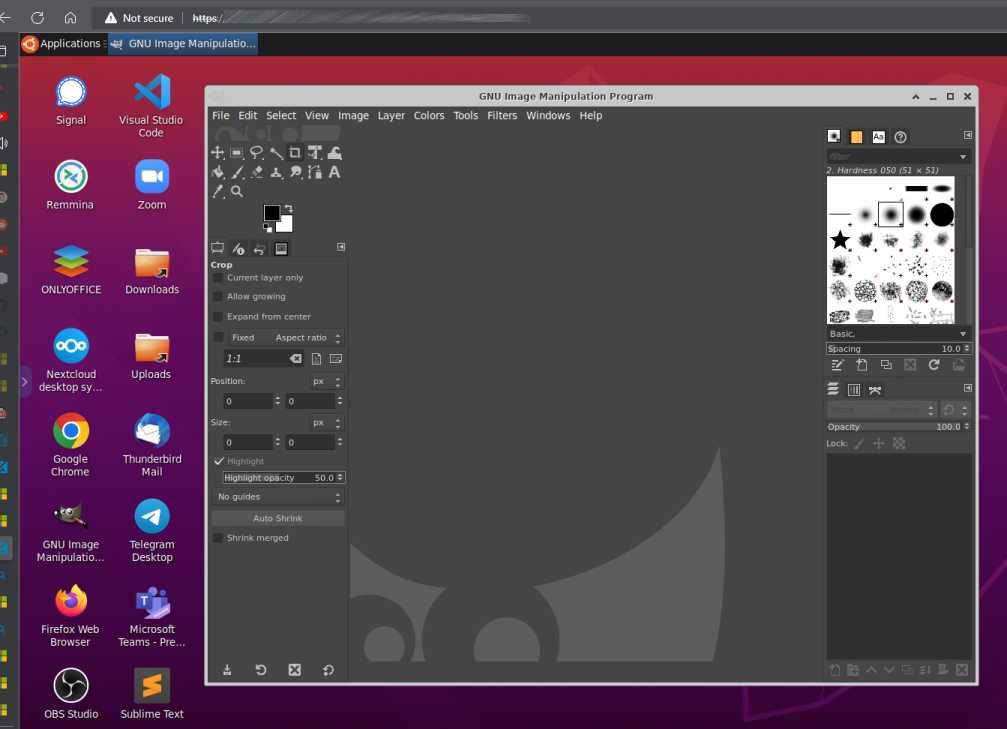
For example using Kasm to run Ubuntu Desktop, and then starting GIMP within the browser

and more importantly running Chrome, within Edge on my IOS device (or IOS Browser squared) 🙂 Most html 5 devices appear to be supported, but keep in mind how it will be rendered based on the interface being used.
Well I hope this was useful or at least inspires some curiosity. Kasm is a powerful tool and I haven't even touched the power of the administrative interface. But I would like to highlight some very cool features.
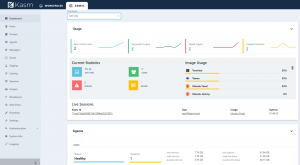
- Dashboard with current resource and image usage
- User and group management
- Multi-zone and environment management
- Session support and session casting
- Web filtering
- Additional authentication options like OpenID and SAML
- and much more
So please spin it up and be bold, be brazen, and start creating your own container applications. Let me know your experience.
Categories
Welcome
Fictal has been created for Musings, Open-Sourcery, Fiction and all permutations in between. The goal is to build upon inclusivity with technology and tomfoolery.
Recent Comments
Categories
#azureimagebuilder #certification #codifying #mushrooms #mycology Azure Azure Bicep Azure Policy bash Bicep codifying Infrastructure DNS IAC Integration JSON Kasm Linux Policy Private Link VDI


Comments
Leave a Comment