Quick Note on Azure Policy
Policy - the eternal topic that managers think is fully implemented but no one has figured it out yet. For most admins taking advantage of the enormous stock of Azure default policies (and initiatives) will meet the requirement but I wanted to highlight the relative ease of creating custom policies. So instead of a step-by-step article of taking business rules and constructing a custom policy I wanted to depict my process.
What started this journey was a simple customer request. They wanted to ensure that any storage account created by their business, tagged "production" must be geo-replicated.
So how did I get there:
- Starting with the fundamentals on Azure Policy open (Overview of Azure Policy - Azure Policy | Microsoft Docs)
- I start by defining the objective of my policy - remember each policy is simply composed of:
- Resource - what is the acting / reacting item - In my example: this is a Storage account but the tags themselves also should be considered
- Evaluator (and sort of Initiator) - what defines the alignment with my policy - In my example: If I have a Storage account that is not Geo replicated (GRS, RAGRS, etc.), and is tagged as "Production"
- Actions> - If my requirements are not met what do (remediate, alert, or (hopefully not) treat as an exception). In my example: migrate the Locally Redundant Storage to Geo-Redundant Storage.
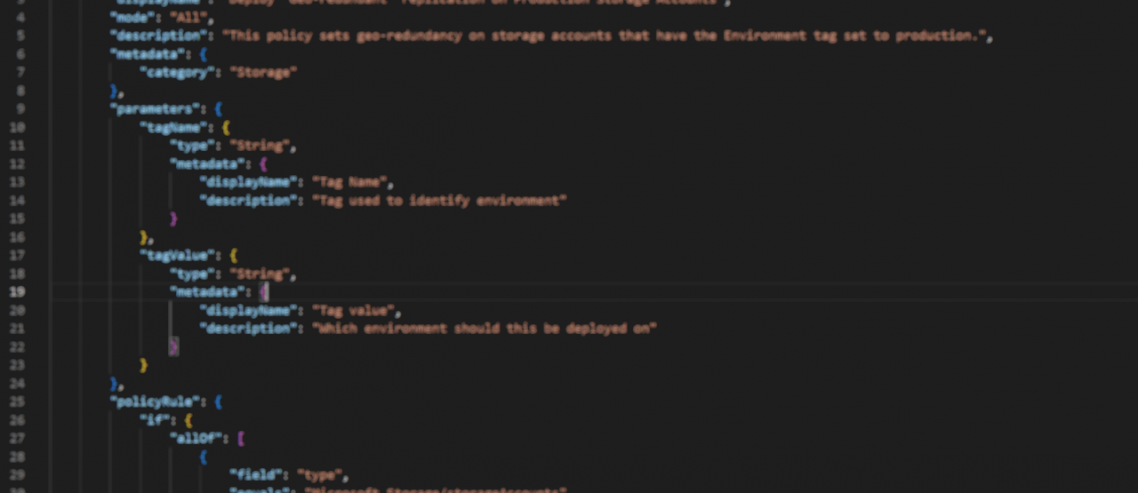
- Next, I ensure I am not reinventing the wheel by reviewing the default policies. If I don't find what I am looking for, I use open-source and purloin from Community-Policy/Policies at master · Azure/Community-Policy (github.com). This may not have exactly what I am looking for but typically I can patchwork Resources, Evaluators, and Actions together based on other Policies.
- Once I have the complete Json I determine how I want to add the Policy into Azure. This is a weird step because either I am deploying the full Json via the portal using the full definition or via IaC (like CLI, or PowerShell) and breaking out the rules against the parameters, but this is NOT the assignment.
Once I have the custom rules, I have two more steps:
- Assign the rule - identify the right scope (Management Group, Subscription, Resource Group), and add my implementation-specific parameters. In my example: I used the Key "environment" must equal "production", on my subscription
- (Re)action - action from my step above, but specific to this assignment. So I may have the action pop out an Alert but I still must determine what to do with it. I can: Ignore, manually resolve, remediate (with automation), or treat it as an exception. In my example: I added in Remediation to allow the "Deploy if not exist" action to continue.
For more information and the code please see my example repository here - tekgnu/CustomPolicies (github.com)
My Example:
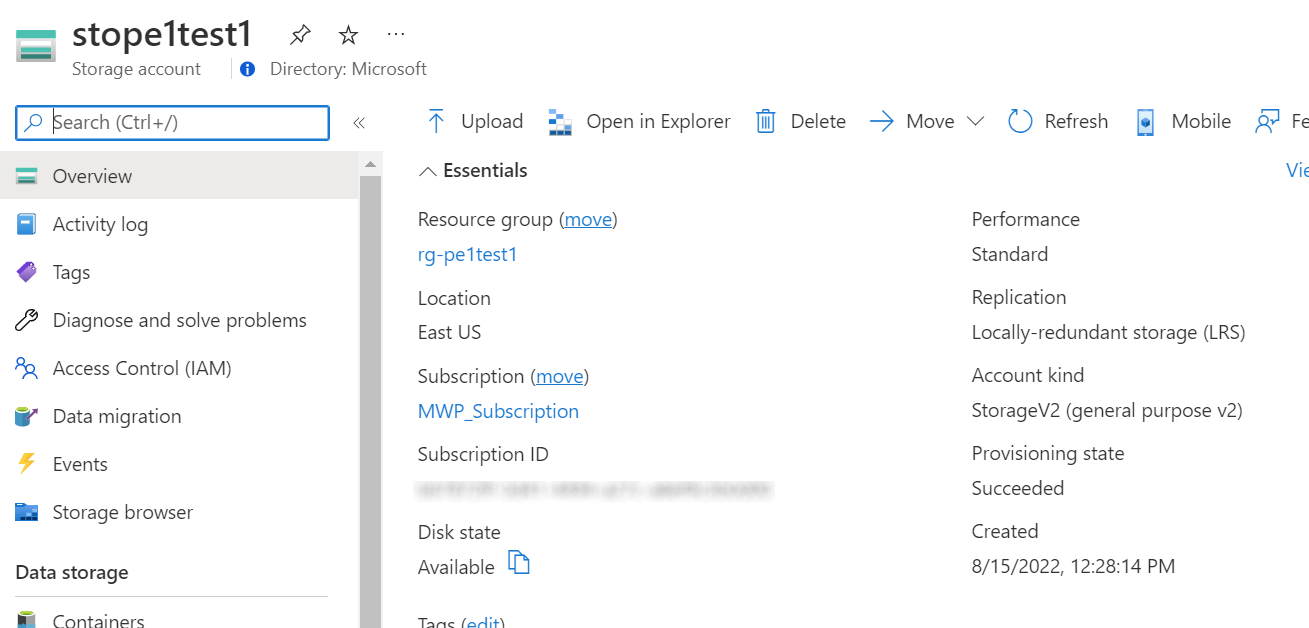
1. Production Storage Account with Locally Redundant Storage.
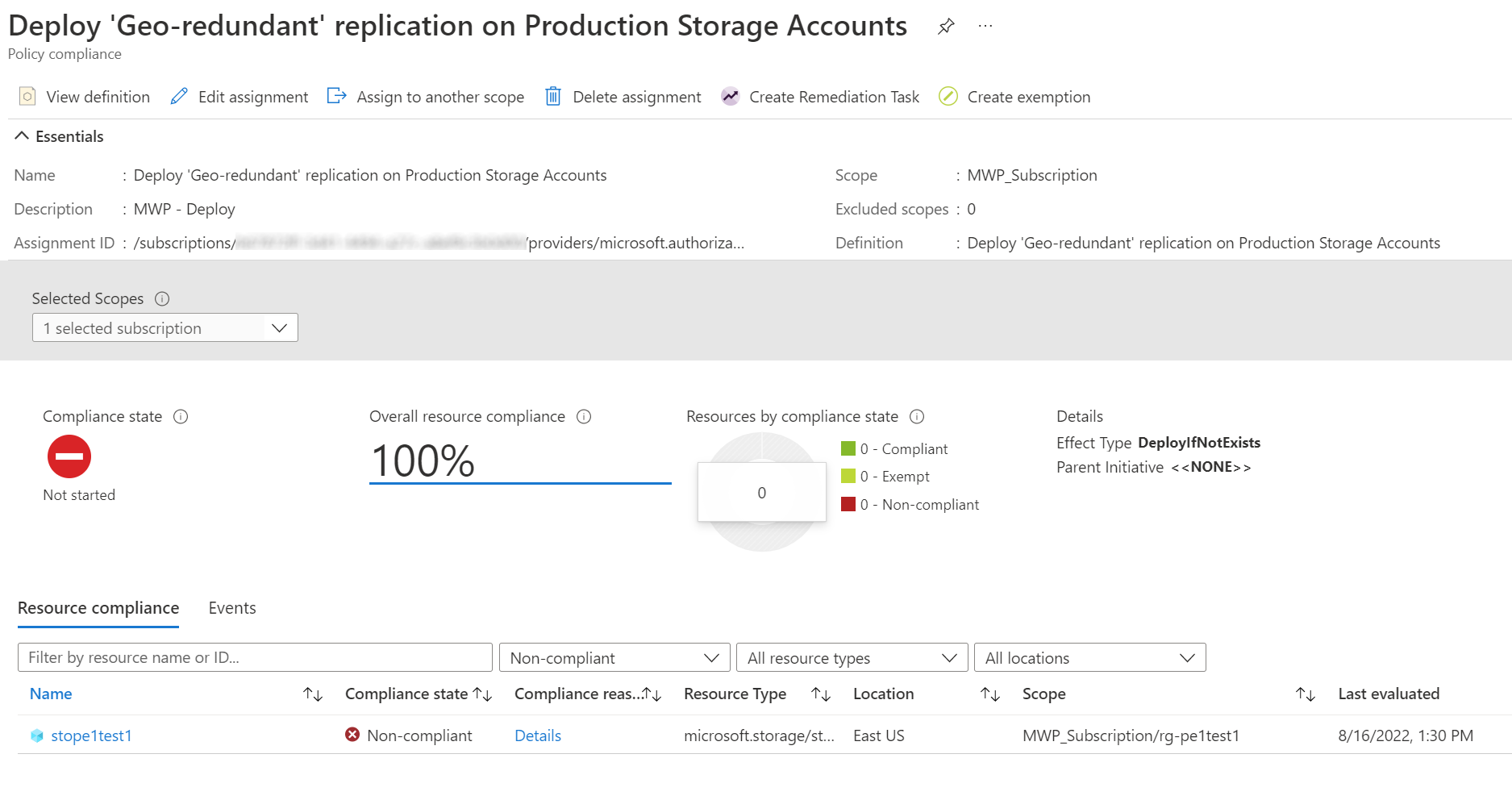
2. Policy evaluating the storage account as non-compliant.
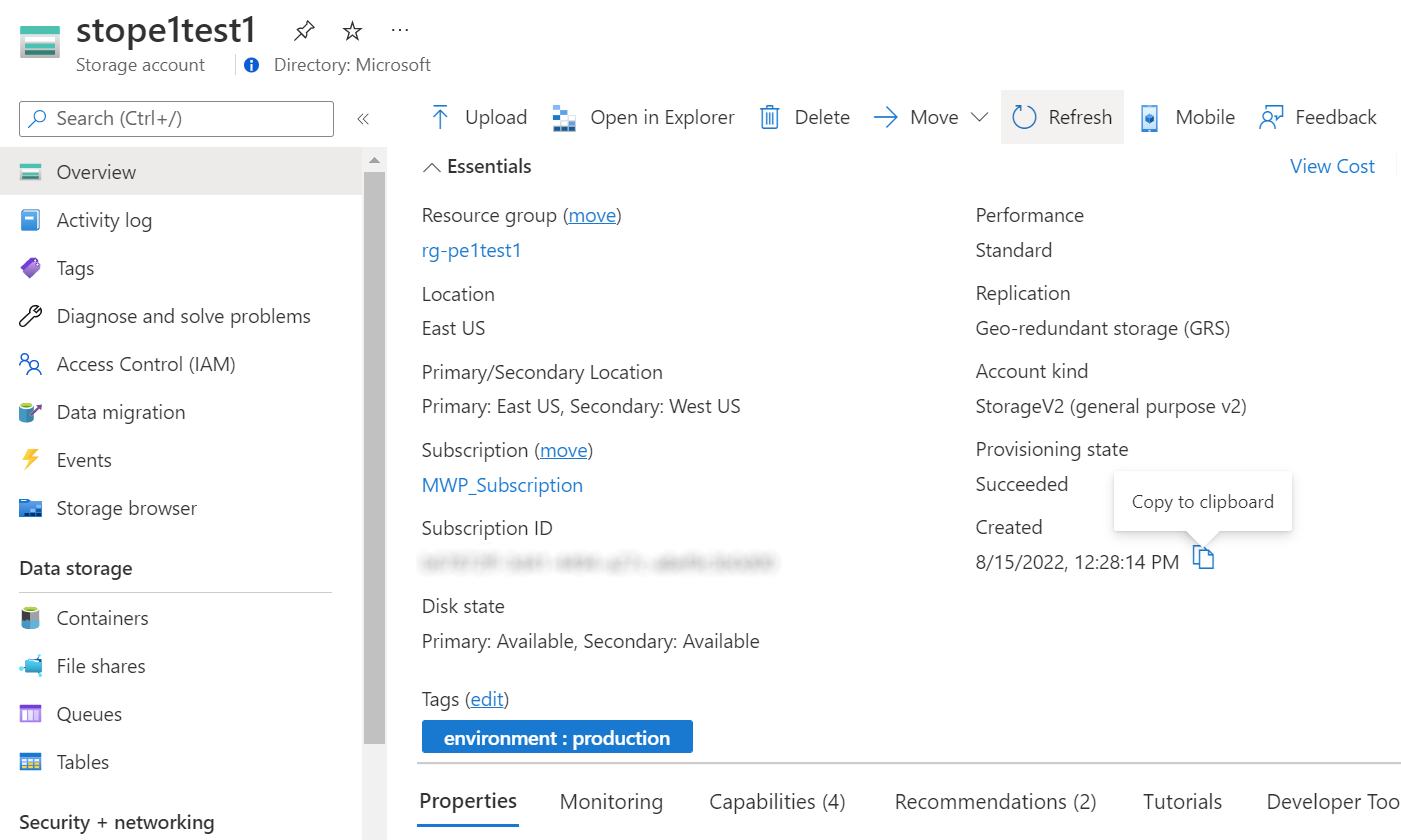
3. Remediation on the deploy if not exist.
Categories
Welcome
Fictal has been created for Musings, Open-Sourcery, Fiction and all permutations in between. The goal is to build upon inclusivity with technology and tomfoolery.
Recent Comments
Categories
#azureimagebuilder #certification #codifying #mushrooms #mycology Azure Azure Bicep Azure Policy bash Bicep codifying Infrastructure DNS IAC Integration JSON Kasm Linux Policy Private Link VDI

Comments
Leave a Comment